Face Match
Instantly confirm the person behind the screen by matching a selfie to a trusted reference (ID photo, prior selfie, or NFC chip portrait).
Problem
Why Face Matching matters
ID checks don’t prove ownership
A document can look valid even if the person presenting it isn’t the holder. Face Match links a live selfie to the ID portrait to confirm it’s the same person.
Selfie alone isn’t enough
Without a trusted reference, basic selfie steps are easier to manipulate. Face Match compares the selfie to a verified source (ID/NFC/prior selfie) for stronger assurance.
Impersonation scales fast
Fraud rings reuse identities and mule networks to open accounts in bulk. Face Match helps stop repeated impersonation by validating the face behind each attempt.
High-risk actions need step-up
Password resets, device changes, and withdrawals are where takeovers happen. Face Match enables quick step-up verification before sensitive actions are approved.
Manual review doesn’t scale
More exceptions mean slower onboarding, higher costs, and inconsistent decisions. Face Match automates identity confirmation to reduce escalations and speed up decisions.
You need auditable proof
Compliance teams must justify approvals, rejections, and re-checks. Face Match returns clear match results and evidence that supports audits and investigations.
How it works
Match the Face Behind the ID
Capture a selfie, compare it to a reference, return a match decision.
Step 1
Capture an ID document
User scans a government-issued ID to extract and validate identity data.

Step 2
Complete a liveness check
The user completes a short liveness check to confirm real presence and detect spoofing attempts.
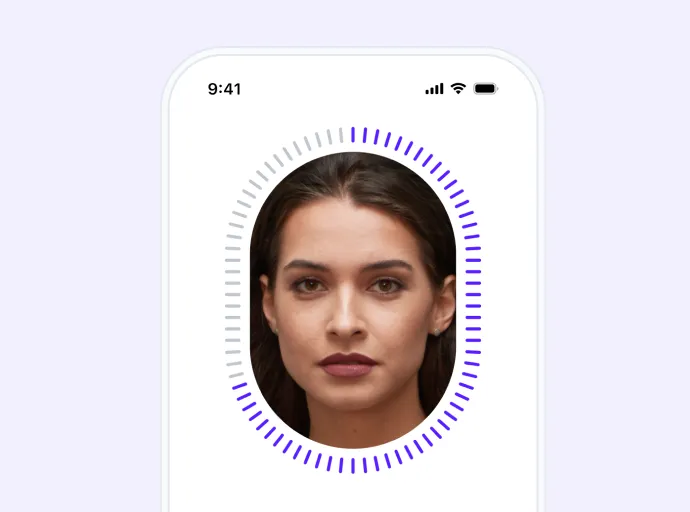
Step 3
Face Match: liveness to ID photo
We compare the liveness capture to the ID portrait (or NFC chip photo) to confirm it’s the same person.

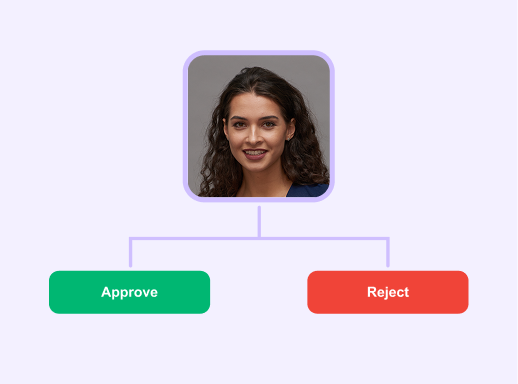
Step 4
Decision
Automatically approve, reject, or route to additional checks based on your rules and risk thresholds.
Use Cases
Explore How Industries Use Face Match
Reduce impersonation and account takeovers across industries with quick selfie-to-reference matching
Security & Compliance
Certified security. Enterprise-ready
Backed by industry standards and security practices to support regulated and high-trust Face Match flows.








FAQ
Frequently asked questions
Everything you need to know about the product and billing.
What is Face Match and what problem does it solve?
Face Match confirms that the person completing a verification is the legitimate holder of an identity. It compares a live selfie to a trusted reference such as an ID document photo, NFC chip portrait, or a previously verified selfie to prevent impersonation and account misuse.
How is Face Match different from basic selfie checks?
A basic selfie confirms presence but not ownership. Face Match compares the selfie against a verified reference, providing stronger assurance that the person behind the screen is the same individual tied to the identity record.
How does Face Match protect against impersonation and account takeovers?
Face Match blocks attempts where valid documents are used by the wrong person. It is commonly applied during onboarding, account recovery, device changes, and withdrawals to stop mule accounts, reused identities, and takeover attempts before they succeed.
Does Face Match include liveness detection?
Yes. Face Match is paired with liveness checks to confirm real-time presence before comparison. This reduces the risk of spoofing using photos, videos, or injected media and strengthens overall match reliability.
Can Face Match be used as a step-up verification for high-risk actions?
Yes. Face Match is designed for step-up scenarios such as password resets, profile changes, payouts, or suspicious behavior. It adds strong identity confirmation without forcing a full re-onboarding flow.
How are Face Match results documented for compliance and audits?
Face Match returns clear match decisions with supporting evidence and timestamps. Results are stored as part of the verification record, giving compliance teams auditable proof for approvals, rejections, and follow-up checks.
See Liveness Check in action
Stop identity spoofing with configurable liveness that keeps onboarding fast. Get a quick walkthrough tailored to your business and industry.
